Economy & Markets
17 min read
Microsoft Most Impersonated Brand in Q4 2025 Phishing Attacks, Reveals CPR
CXOToday.com
January 20, 2026•2 days ago
AI-Generated SummaryAuto-generated
Microsoft was the most impersonated brand in phishing attempts during Q4 2025, accounting for 22% of attacks. Google and Amazon followed as top targets. Attackers exploit trust in these platforms for credential theft, with sophisticated tactics like lookalike domains and AI-generated content. Facebook re-entered the top 10, indicating increased interest in social media account takeovers.
Check Point Research (CPR) today released its Brand Phishing Ranking for Q4 2025. The latest findings show that Microsoft once again ranked as the most impersonated brand, appearing in 22% of all phishing attempts during the quarter. This continues a multi-quarter trend in which attackers systematically abuse widely used enterprise and consumer platforms to steal credentials and gain initial access.
Google (13%) and Amazon (9%) followed in second and third place respectively, with Amazon’s rise driven largely by Black Friday and holiday-season activity. After several quarters of absence, Facebook (Meta) re-entered the global top 10, landing in fifth place, signaling increased attacker interest in social-media account takeover and identity theft.
Omer Dembinsky, Data Research Manager at Check Point Research, says: “Phishing campaigns are becoming increasingly sophisticated, leveraging polished visuals, AI-generated content, and highly convincing domain lookalikes. The fact that Microsoft and Google remain the top targets shows how valuable identity-based access has become for attackers. Meanwhile, the return of brands like Facebook and PayPal underscores how cybercriminals adapt quickly, shifting toward platforms where trust and urgency can be exploited. To counter these evolving tactics, organizations must adopt a prevention-first approach that combines AI-driven detection with strong authentication and continuous user awareness.”
Top 10 Most Imitated Brands in Q4 2025
Microsoft – 22%
Google – 13%
Amazon – 9%
Apple – 8%
Facebook (Meta) – 3%
PayPal – 2%
Adobe – 2%
Booking – 2%
DHL – 1%
LinkedIn – 1%
The persistent dominance of Microsoft and Google reflects their essential role in identity, productivity, and cloud services—making associated credentials particularly valuable to cybercriminals.
Phishing Campaigns Observed in Q4 2025
Roblox: Phishing Targeting Children and Gamers
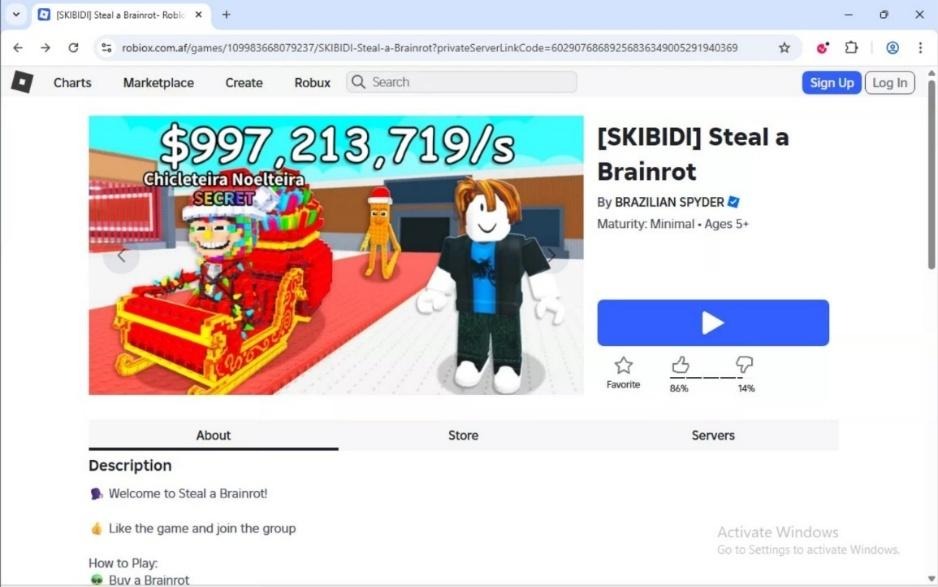
In Q4 2025, CPR identified a Roblox-themed phishing campaign observed via user browsing activity. The malicious site was hosted at a lookalike domain, robiox[.]com[.]af, differing from the legitimate roblox.com by a subtle letter substitution.
Fraudulent Roblox Game Page
The landing page presented a fake Roblox game titled “SKIBIDI Steal a Brainrot”, complete with realistic visuals, ratings, and a prominent “Play” button. The content closely mimicks one of the most popular games currently on the Roblox platform and was clearly designed to appeal to children—a core segment of the platform’s user base.
Fraudulent Roblox Login Page
When users attempted to access the game, they were redirected to a second-stage phishing page that replicated the official Roblox login interface. Credentials entered on the page were silently harvested, while the user remained on the same screen with no visible indication of compromise.
Netflix: Account Recovery as a Lure
Fraudulent Netflix Page
CPR also identified a Netflix-impersonation phishing site, hosted at netflix-account-recovery[.]com (currently inactive). The domain was registered in 2025, in contrast to the legitimate netflix.com, which dates back to 1997.
Legitimate Netflix Page (netflix.com/LoginHelp)
The phishing page closely mirrored Netflix’s official login and account recovery interface, prompting users to enter their email address or mobile number and password. The objective was straightforward: credential harvesting for account takeover, potentially enabling resale or further fraud.
Facebook (Meta): Localized Credential Theft
Fraudulent Facebook (Meta) Page
In another campaign observed during Q4 2025, CPR detected a Facebook-themed phishing page delivered via email and hosted on facebook-cm[.]github[.]io. The page impersonated Facebook’s login portal and was presented entirely in Spanish, using familiar branding, layout, and authentication prompts. Users were asked to enter their email address, phone number, and password, which were subsequently harvested by the attackers to enable unauthorized account access and potential downstream abuse.
Why Brand Phishing Continues to Succeed
Brand phishing remains effective because it leverages user trust in familiar digital services. Attackers increasingly rely on:
Lookalike domains with subtle character changes
Professionally designed pages mimicking real login flows
Multi-stage deception paths that appear legitimate
Emotional triggers such as urgency, reward, or brand familiarity
As identity becomes the core attack surface in today’s cloud-driven environments, phishing continues to serve as a key initial access vector for both consumer fraud and enterprise breaches.
Check Point Research provides leading cyber threat intelligence to Check Point Software customers and the greater intelligence community. The research team collects and analyzes global cyber-attack data stored on ThreatCloud to keep hackers at bay, while ensuring all Check Point products are updated with the latest protections. The research team consists of over 100 analysts and researchers cooperating with other security vendors, law enforcement and various CERTs.
Check Point Software Technologies Ltd. utilizing AI-powered cyber security solutions to safeguard over 100,000 organizations globally. Through its Infinity Platform and an open garden ecosystem, Check Point’s prevention-first approach delivers industry-leading security efficacy while reducing risk. Employing a hybrid mesh network architecture with SASE at its core, the Infinity Platform unifies the management of on-premises, cloud, and workspace environments to offer flexibility, simplicity and scale for enterprises and service providers.
Rate this article
Login to rate this article
Comments
Please login to comment
No comments yet. Be the first to comment!
